NAC
Suzhou Metalogic Information Technology Co.,Ltd 2018-11-08 14:15:59 Author:SystemMaster
The source definition of information security requirements according to the international standard ISO/IEC 17799:2005 "Information Technology-Information Security Management Business Code". There are three main sources of information security needs: legal, prescribed and contractual requirements; From the perspective of enterprise IT management, the first and second sources are mainly legal and business-related hard requirements, that is, the content that must be met in IT security construction. The third source is the various risks faced by information systems and their security protection and security management.
Requirements of laws and regulations for information security
At present, among the laws and regulations in force in China, 65 are directly related to information security, of which 18 are laws and regulations regulating information security, such as the Regulations of the People's Republic of China on the Security and Protection of Computer Information Systems,there are also normative and guiding documents, such as the "Administrative Measures for the Protection of Information Security Levels." Due to the early development of information technology in developed countries such as Europe and the United States, the corresponding or close laws, regulations and standards are more complete and strict. Such as the Sarbanes Act and the ISO 27001 Information Security Management System, which cover various areas such as network and information system security, computer virus and harmfulness program prevention, and information security crime sanctions. The requirement of the state for information security in the aspect of laws and regulations is the hard requirement of the enterprise information security construction, so the importance of laws and regulations makes it the primary requirement of the enterprise information security construction.
Administrative Measures on Information Security Hierarchy Protection
The security protection level of information system is defined from two aspects: technology and management. Related content of intranet security includes:Terminal access control
Border integrity inspection
Host ID
Intranet access control
Malicious code prevention and system security management, etc.
Sarbaes-Oxley Act
Sarbanes-Oxley Act , which imposes financial restrictions on U.S. listed companies, sets strict requirements for IT governance, IT internal control, and external auditing. The Sarbanes-Oxley Act covers a very comprehensive range of management content, of which Section 404 (Management Assessment of Internal Controls) explicitly requires control within the company.National and foreign authorities have long defined the laws and regulations governing access control for intranet security. From the perspective of building an IT internal control system, and drawing on the international internal control framework and international best practice experience, we can build a systematic, standardized, auditable, and sustainable improvement IT internal control system.
ISO 27001 Information Security Management System
ISO27001 states that information security is achieved through the implementation of combined controls to prevent various threats to information and ensure business continuity, minimizing the risk of damage to your business and maximizing your return on investment and business opportunities. Security controls can be policies, conventions, procedures, organizational structures, and software functions. The management specifications and equipment requirements specifications for access networks are clearly indicated in ISO 27001.
Why do we need NAC network access?
Asset management confusionPC How many PCs do we have?How many printers do we have?How many VOIP phones do we have?What kind of network equipment do we have?What are some unknown devices inside our company?
Enterprise employees and visitors share corporate resourcesVisitor PCs can access corporate resources with IPGuest PCs consume a lot of internal corporate bandwidthThere is a risk of leakage of internal resourcesEmployee PC health is difficult to controlThe employee PC does not open/install anti-virus software and is vulnerable to viruses.The employee's PC-side virus database has not been upgraded to the latest version, and the latest virus is difficult to prevent and control.Employee PC running non-compliant application
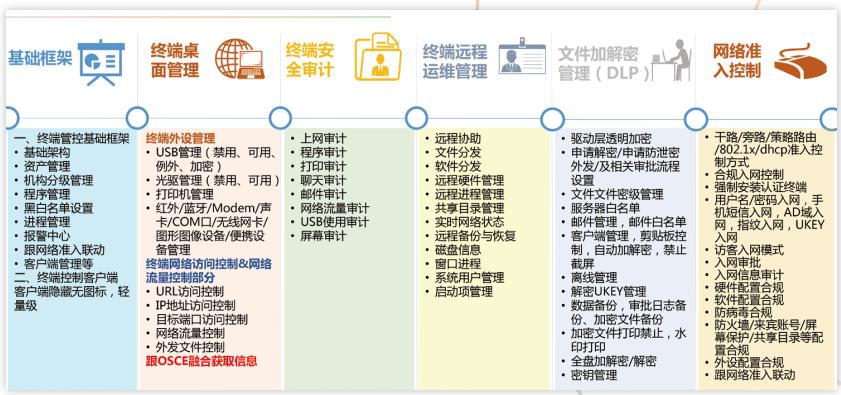 Help IT achieve:
Help IT achieve:
Enterprise employees and visitors share corporate resourcesVisitor PCs can access corporate resources with IPGuest PCs consume a lot of internal corporate bandwidthThere is a risk of leakage of internal resourcesEmployee PC health is difficult to controlThe employee PC does not open/install anti-virus software and is vulnerable to viruses.The employee's PC-side virus database has not been upgraded to the latest version, and the latest virus is difficult to prevent and control.Employee PC running non-compliant application
 Help IT achieve:
Help IT achieve:




